AQUILA - Setup Integration from Auth0
Auth0 Integration Guide
Integrate Auth0 to ingest identity-related logs such as login attempts, user authentications, MFA usage, and blocked requests to support identity threat detection and correlation.
Credentials & API Access Setup (Auth0)
Before setting up the integration, create a Machine-to-Machine application in Auth0 to collect logs via API.
Steps:
-
Log in to the Auth0 Dashboard.
-
Go to Applications → APIs.
-
Create or select your Management API (typically named
Auth0 Management API). -
Under Machine-to-Machine Applications, authorize your log collector app.
-
Take note of the following credentials:
-
Auth0 Domain (e.g.,
your-tenant.us.auth0.com) -
Client ID
-
Client Secret
-
Audience: usually
https://your-tenant.us.auth0.com/api/v2/
-
| Required Detail | Value |
|---|---|
| Auth0 Domain | your-tenant.auth0.com |
| Client ID | From your M2M Application |
| Client Secret | From your M2M Application |
| Audience | https://your-tenant.auth0.com/api/v2/ |
| Token URL | https://your-tenant.auth0.com/oauth/token |
Permissions Reference (Auth0 M2M App)
Ensure the app is granted the following scopes from the Auth0 Management API:
| Data Stream | Scope Required |
|---|---|
| Login Activity | read:logs, read:users |
| MFA Logs | read:logs |
| Failed Logins | read:logs |
| User Access Logs | read:users, |
🔐 You can test token access using Postman or curl before ingesting.
Aquila Integration Configuration
AQUILA – Microsoft 365 Integration
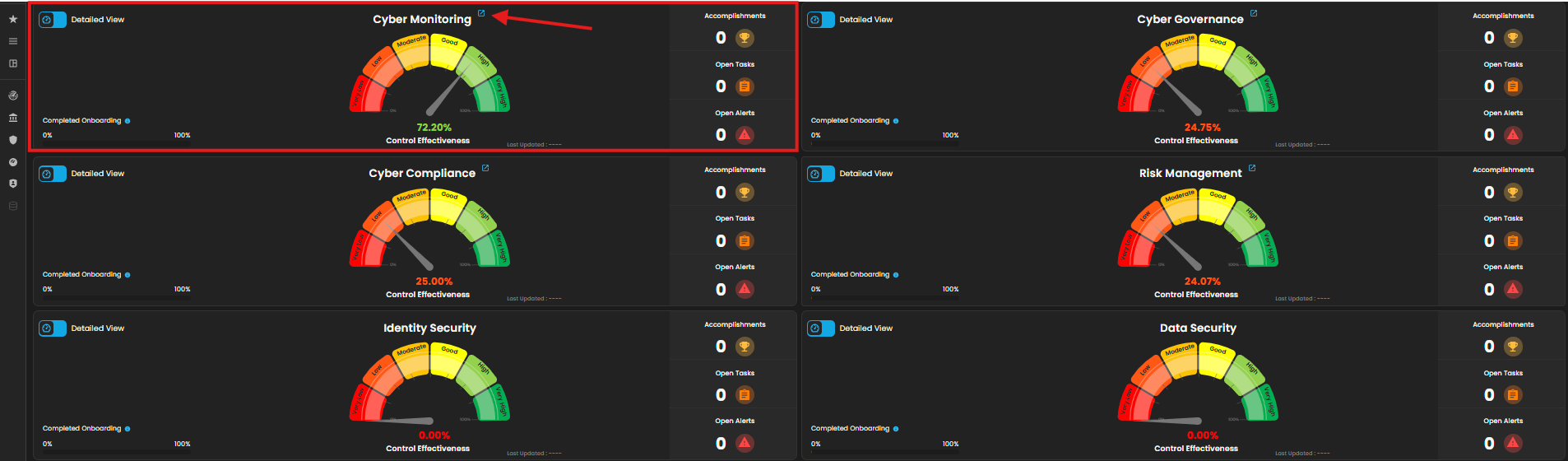
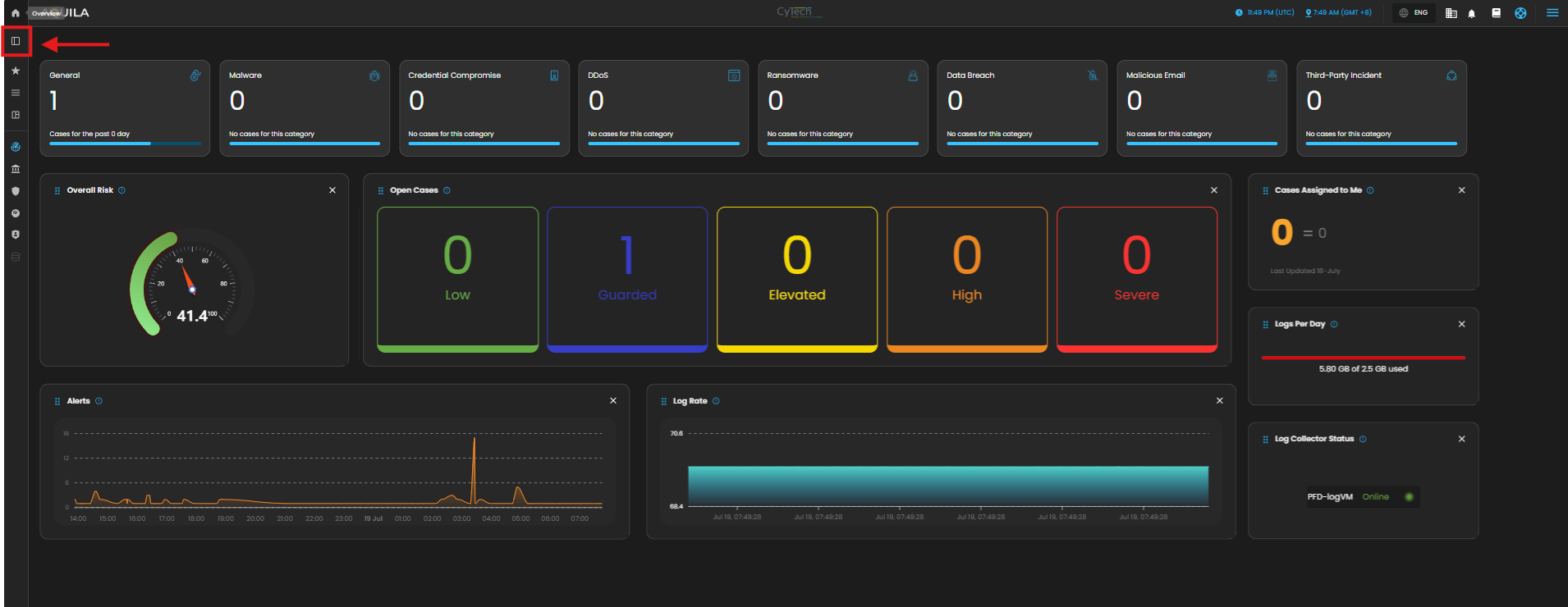
1. Log in to AQUILA click here - CyTech - AQUILA. Choose Cyber Monitoring and click the small arrow icon to redirect you to the Cyber Monitoring Dashboard.
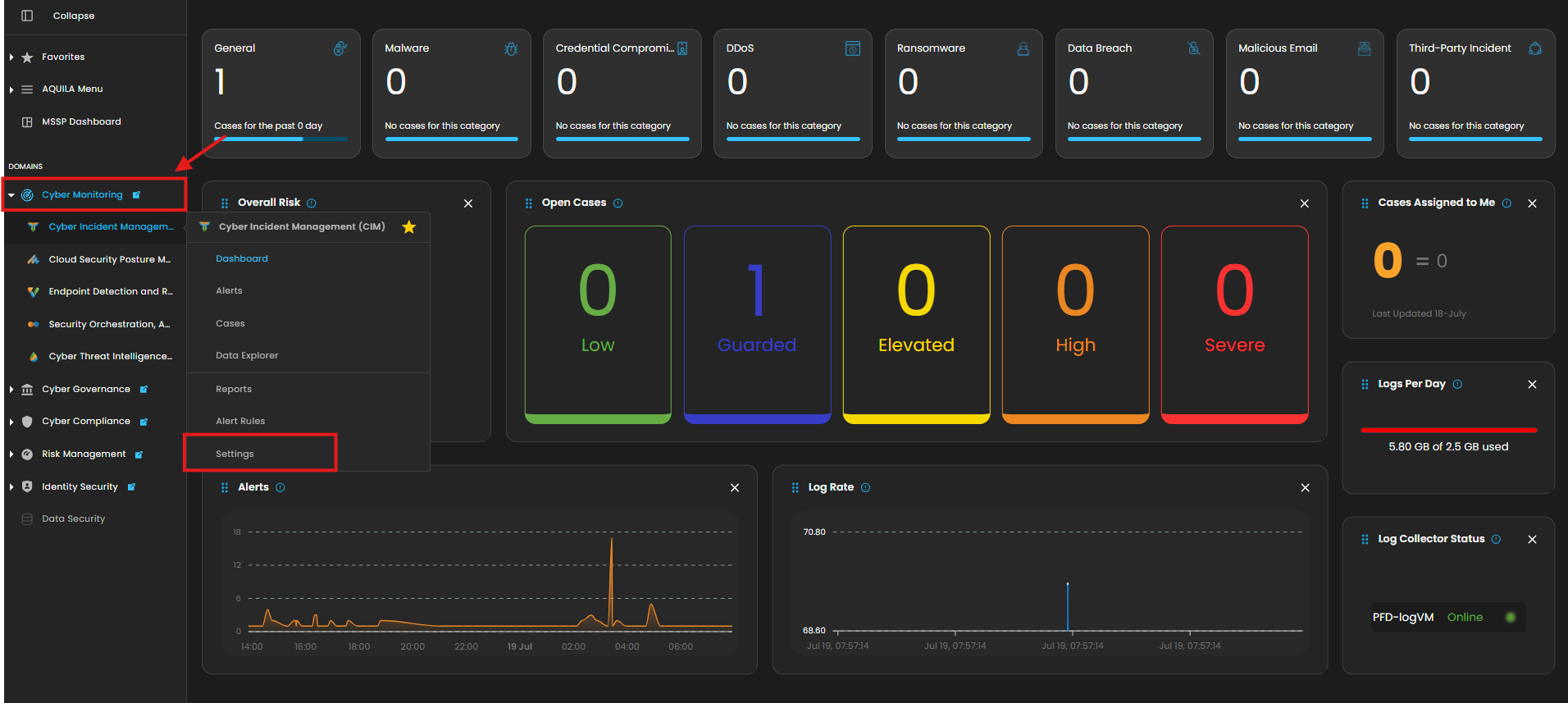
2. In the dashboard, choose Cyber Incident Management (SIEM and XDR).
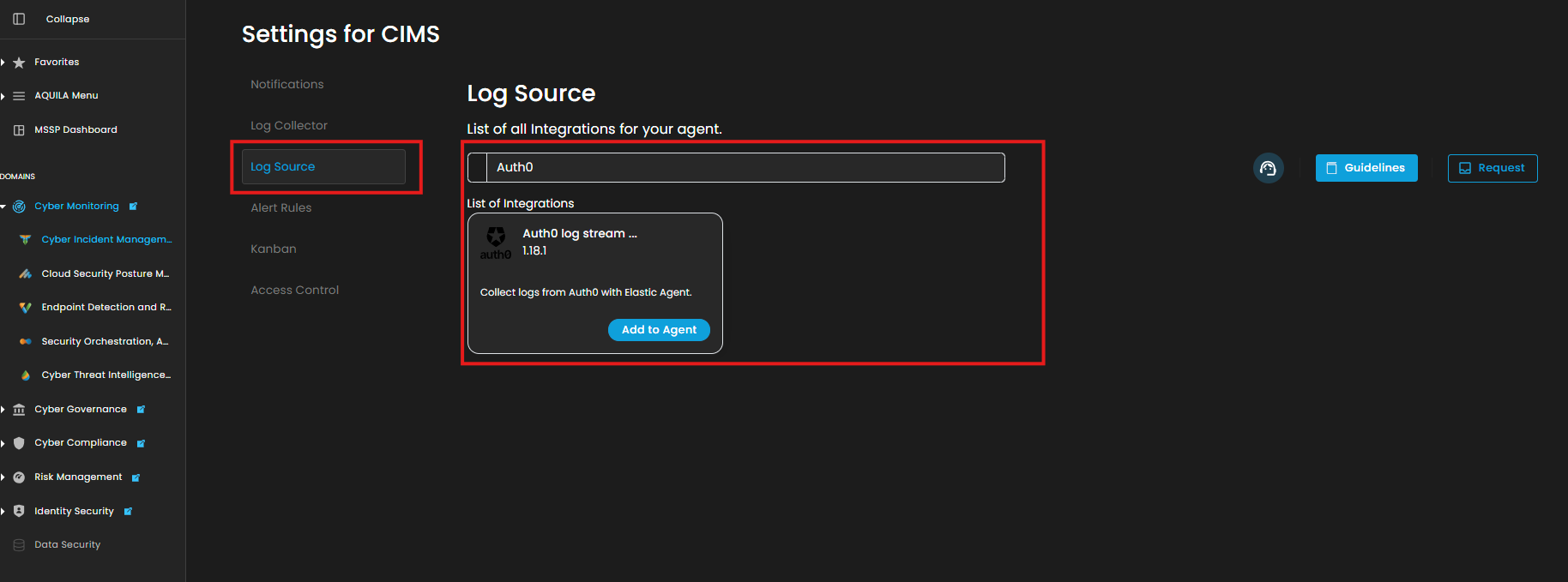
5. Click the "Settings, and Navigate through Settings>Log Source>Search Bar>Add to Agent.
6. Choose your Log Collector. (If you not yet installed your Log Collector please refer to this link - Log Collector Installation.)
Step 7 and below is just a reference, this is still incomplete. Thorough investigation and research in progress to understand the flow and credentials required.
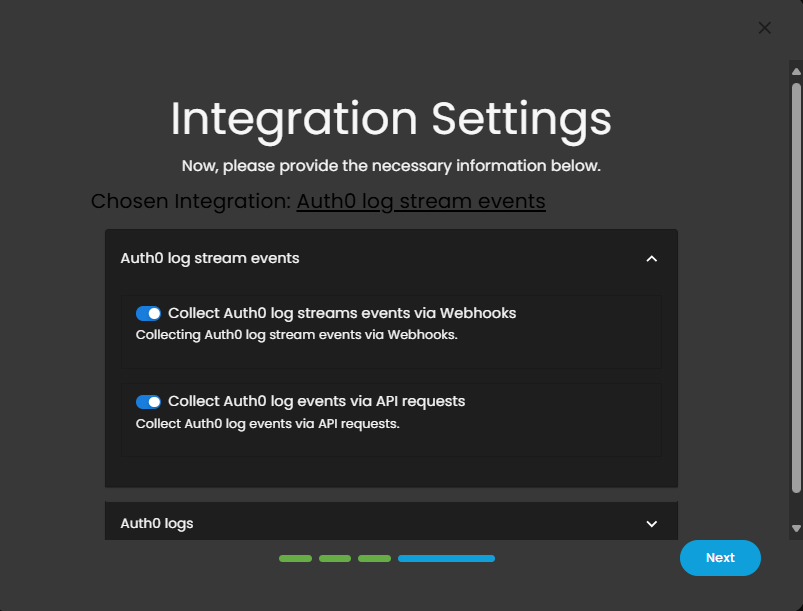
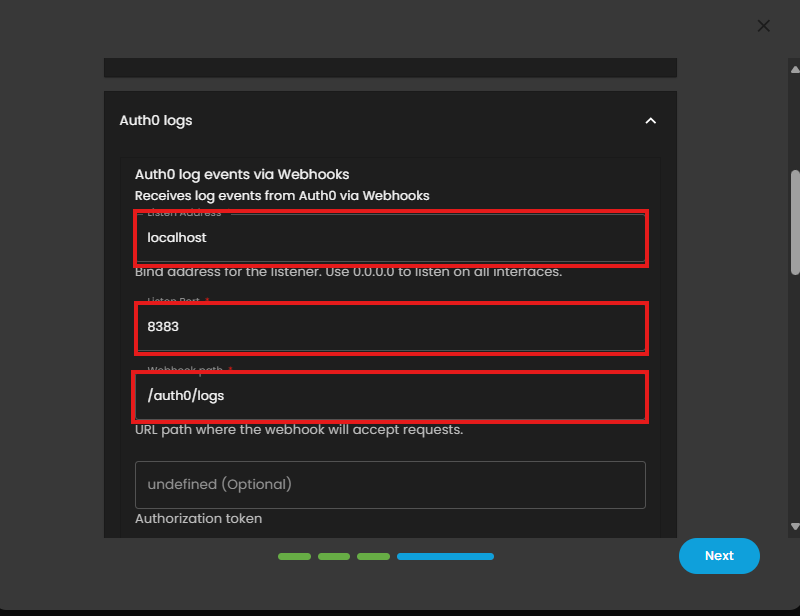
7. In the integration settings follow the instructions given below.
- Click the drop arrow to display the contents needed for the integration setup.
- In the Office 365 logs section > Disable > Collect Office 365 audit logs
- Scroll down and go to Microsoft Office 365 audit logs section.
- Input the credentials for Directory(tenant) ID, Application(client) ID and the Client Secret Value.
- Finally, click Next to install the log source integration.
8. Wait for the Successfull window to display, this will confirm the successfull integration.
If you need further assistance, kindly contact our support at support@cytechint.com for prompt assistance and guidance.