Cyber Security Risk Management
Overview:
Cyber risk management is a systematic approach to identifying, assessing, and mitigating risks associated with cybersecurity threats. It involves recognizing potential vulnerabilities and threats, evaluating their impact and likelihood, and prioritizing them based on their significance. Strategies are then developed and implemented to reduce or manage these risks, including technical solutions, policies, and procedures. Continuous monitoring and regular reviews ensure that risk management efforts remain effective and adapt to the evolving threat landscape, thereby protecting an organization's information assets and maintaining business continuity.
Navigate to the module:

- Under Cyber Assessment, click on Cyber Security Risk Management
How to Register an Identified Risk:
From the main dashboard page, select "Risk Assessment" from the side panel, and then click on "Register Identified Risk."
- From here choose whether the risk is a Critical Core Business Function (CBF), non-critical CBF, or Both Critical and Non-Critical CBF.
- Once the information is filled on, click next.
- Once all these information have been filled out, that means you have successfully identified a risk. This would then be show on the risk assessment dashboard.
Task Management Dashboard:
The task management dashboard is a central tool for organizing, tracking, and prioritizing tasks within a project or team, offering a visual overview of deadlines, task statuses, and assigned team members. It often includes features like lists or Gantt charts to facilitate efficient planning and workflow management. When integrated with a risk management module, the dashboard allows users to link specific tasks to identified risks, monitor the implementation of risk mitigation strategies, and track progress on risk-related actions. This integration ensures that risk management activities are effectively managed and aligned with overall project goals, helping teams address potential issues proactively and maintain project timelines.
How to add a task:

- In the task management dashboard, find the "Create Task" button on the right-hand side, indicated by the red arrow. Click this button to open a modal where you can enter details about the new task. After filling out the necessary information, click "Save" to create the task. The newly created task will then appear on the dashboard, complete with all relevant details and its corresponding Gantt chart representation.
Risk Management Dashboard:
Risk management in cyber risk management involves identifying, assessing, and prioritizing potential threats to an organization's information systems and data. This process includes evaluating the likelihood and impact of various risks, implementing controls to mitigate those risks, and continuously monitoring and adjusting strategies as threats evolve. A risk repository plays a crucial role in this framework by serving as a centralized database where all identified risks, their assessments, mitigation measures, and status updates are documented. This repository enables organizations to maintain a comprehensive view of their risk landscape, track the effectiveness of their risk management strategies, and ensure that risk information is accessible for informed decision-making and compliance purposes.
To access the timeline, files, and comment for a specific risk, click on any values on the risk repository to view more information.
Dashboard:
- Provides an overview of the organization's current risk status.
Risk Score:
- Represents the overall risk level of the company.
- Clicking on the risk score provides a detailed breakdown of severity levels.
Summary of Findings:
- Provides insights into how the country prevents, withstands, and recovers from cyber-attacks.
- Click on view all to access more details about the summary of findings
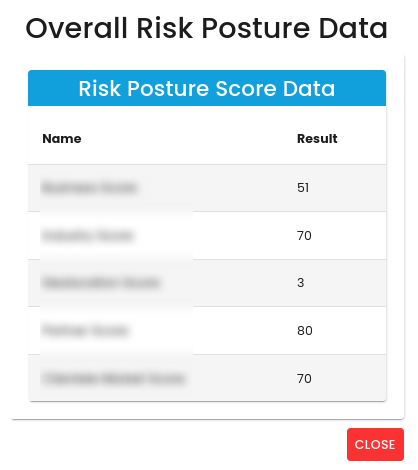
Risk Posture of your organization:
- Presents the risk posture of the organization, including risks that are mitigated, transferred, avoided, or accepted.
Overall Impact Breakdown:
- Illustrates how the organization handles identified risks.
Click on any of the different impacts to view more details.
CRAMTM Live View:
- Offers a dynamic presentation of the organization's structure:
- The center represents the organization.
- Three surrounding circles depict Critical Business Processes.
- Connected circles represent Critical Business Functions.
- Other nodes represent business vectors.
Click on any of the surrounding nodes to view more details
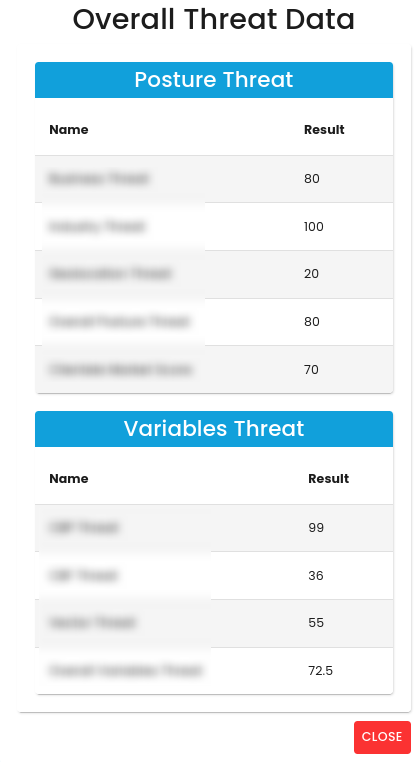
Overall Probability Breakdown:
Each point on the chart illustrates various factors that influence the probability of cyber risk. To view detailed information about them, click on any point on the chart.
Asset Identification:
CRAM™ (Cyber Risk Assessment and Management) building blocks form a comprehensive framework for addressing cyber risks. They include Risk Identification to recognize potential threats and vulnerabilities, Risk Assessment to evaluate and prioritize these risks based on impact and likelihood, Risk Mitigation to develop strategies and controls to reduce or eliminate risks, Risk Monitoring to track the effectiveness of these strategies and adapt to evolving threats, Risk Communication to ensure that information about risks and mitigation efforts is clearly conveyed across the organization, and Risk Governance to oversee and manage the overall risk management process. Together, these components provide a structured approach to effectively manage and mitigate cyber risks.
Geo Location:
A geographic map incorporating metrics like Market Vulnerability Level, Market Threat Level, Market Impact Level, and Market Cyber Resiliency offers a visual representation of cyber risks across different regions or markets. This map helps organizations identify areas with high susceptibility to threats, understand the intensity of cyber threats in various locations, evaluate the potential impact of cyber incidents, and gauge the resilience of different markets in responding to and recovering from attacks. By visualizing these factors, the map aids in prioritizing risk management efforts, allocating resources effectively, and tailoring strategies to address specific regional needs and vulnerabilities.
If you need further assistance, kindly contact our support at info@cytechint.com for prompt assistance and guidance.